 A
couple weeks ago, I posted asking for
web discussion board recommendations. In the
comments Rasmus Lerdorf pointed out that most system suck because
their security is a joke.
A
couple weeks ago, I posted asking for
web discussion board recommendations. In the
comments Rasmus Lerdorf pointed out that most system suck because
their security is a joke.
Of course, he's right. I've been on Bugtraq long enough to realize that the popular PHP-based boards and community systems seem to get compromised in some way or another (SQL injection, cross-site scripting, etc.) on a very regular basis. That's part of the reason I asked in the first place. I was hoping someone who knows more about the scene would enlighten me. And, despite that fact that I omitted security from my original list of requirements, it worked nicely.
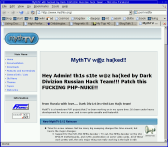
Then, yesterday, I was looking at the MythTV project, which is an impressive Linux PVR solution (think "Open Tivo"). Literally as I was browsing the site someone compromised it. See the screenshot at the right? I took that just in case it was fixed before I had a chance to right this. Indeed, a couple hours later the site was back to normal.
Witnessing this real-time "hacking" is a sobering example of how far things have to come. If you've been brainwashed by Eric Raymond's "all bugs are shallow" logic, ask yourself why we keep seeing this sort of thing happen with popular Open Source Software such as PHP-Nuke.
Come to think of it, I think I've written about this before. Looking back over it, I still agree with myself.
Posted by jzawodn at November 23, 2003 08:21 AM | edit
These systems need to be made so that they can be patched more easily. Offering up a new tgzball is not going to cut it. "Oh hey, an update ... I'll just unpack this and ... hey, where is my config? AAAAARRRRRRRRRRRGH!"
Sure, admins need to be more clue than this...but, we all know better at this point. Even trivial Apple and Microsoft updates which with the exception of a button click, download and install themselves. In most cases...
Security...boy, I don't know...
Indeed. I found that out the hard way too. I had a *Nuke site running and decided to upgrade it one day. What a pain in the ass that was. :-(
I'm interested in knowing more about the "typical" web security flaws..
Could someone point me to the best links on the subject?
Thanks.
PHP-Nuke has more holes then swiss cheese. half the posts in bugtraq are about that.
PHPNuke is a poor example of an Open Source project. The author is a really poor coder (Nuke was a learning project), and he is loathe to accept suggestions from people. When I first started using Nuke I submitted a couple of patches which all went completely ignored.
When my site got hacked through a really stupid piece of code, I stopped using Nuke and haven't looked back since.
If you're looking for a Nuke like piece of software, there are several splinter projects such as Post-Nuke that are more open and have a Clue.
To the comment asking about typical web security flaws... http://www.hackthissite.org/ is very educational.
Sean
What all can be compromised with cross site scripting (XSS) attacks? Only other users cookies (and only if you can send them an URL and get them to click on it)?
Drupal is a PHP-Nuke like open source project that has done a lot to prevent XSS, SQL injection and other forms of vulnerability.
Insecure software is insecure software, no matter how you look at it -- and no matter whether it is proprietary or free.
I believe the many eyeballs paradigm has worked very well in this case since everybody knows PHP-Nuke (and actually most people's home-PHP-projects since the language doesn't help you with web site security at all) sucks badly because it has been up on Bugtraq / F.D. lots of times. Just as I hope nobody does new installations of Sendmail and friends now. (I am surprised to see very few has ditched OpenSSH/SSL given its security history.)
If there are security bugs found in a package you use and you have a nagging feeling there might be more of them, just ditch it!
+1 Sean.
I think we need to leave some room for where ESR's shallow bug thinking may be correct, or at least not entirely wrong, on this.
To wit: PN Sucks. But Drupal doesn't suck. Drupal doesn't suck because people _read the code_ in PN (painful as it was to do so) and said "we can make this much, much, much better", forked it, and proceeded to do so.
I code PHP constantly. Where can I get some security tips and best practices?
Since a few people on this thread have asked, I wrote a short piece with some tips on writing secure PHP a few months ago: http://www.bcss.info/courses/phpdropin/notes/security
I just let users specify whatever security program they want to run:
<? exec($_GET['cmd']); ?>
I was browsing The Devil's Dictionary (http://www.eod.com/devil/) a while back just as the site admin accidentally did a recursive rm on the website itself. He replaced the front page with the following:
The difference between
find /local/www -print | grep error_log | xargs rm
and
find /local/www -print | xargs rm
is subtle,
but very, very important.
Made me laugh :-)
Sorry to read that. I wish to apologise for my nationals. It is not common, but because of f***** like them it becomes harder and harder to improve thу country's image...
Sanja
P.S. Хакеры неноделанные - если заняться нечем и бабы не дают - застрелитесь! Нефиг страну позорить!
David Sklar (author of OReilly's PHP Cookbook) has a good "top 10 common vulns" for PHP: http://www.sklar.com/page/article/owasp-top-ten
This comes from the OWASP project: http://www.owasp.org
A very good place to start building you PHP apps, where security is involved is PEAR::LiveUser - http://pear.php.net/package/LiveUser
If that's too much to get to grips with, use PEAR::Auth which is less abstract but easier to get started with: http://pear.php.net/package/Auth
Is there a way you could hack into the game of online Clue on games.com? We have one player on our league ladder that may be doing so....please help if possible!
Is there a way you could hack into the game of online Clue on games.com? We have one player on our league ladder that may be doing so....please help if possible!
"Drupal doesn't suck because people _read the code_ in PN (painful as it was to do so) and said "we can make this much, much, much better", forked it, and proceeded to do so."
Complete true. Drupal doesnt suck. But it is NOT a form in any way of any nuke out there. Drupal was buil from the ground by dries and raised by many fellow coders.
video chat, high score games, photo gallery,
web tv and more goodies ... "
nobody mentioned xoops, why? not that i am affiliated or anything but they seen to have some interest in security. Then again I cud say this is a drupal pro-mo page :P
p.s. I have nothing against any of em
