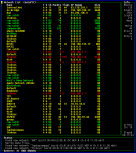
 After yesterday's fun with WarDriving in Toledo, I
saddled up for the ride toward Cleveland along the Ohio Turnpike (from
exit 59 in Toledo to exit 193 at route 44, Ravenna). The results,
again, were interesting. A good mix of commercial and residential
setups. As with yesterday, the Linksys equipment outnumbered the
occasional NetGear and Apple stuff. This time I saw at least one 3com
device too.
After yesterday's fun with WarDriving in Toledo, I
saddled up for the ride toward Cleveland along the Ohio Turnpike (from
exit 59 in Toledo to exit 193 at route 44, Ravenna). The results,
again, were interesting. A good mix of commercial and residential
setups. As with yesterday, the Linksys equipment outnumbered the
occasional NetGear and Apple stuff. This time I saw at least one 3com
device too.
Another amusing thing was that I'd pick up the "flyingj" network when we'd go past some of the truck stops. I didn't expect that.
There were some long patches (20 minutes or so) of finding nothing, but even the rural areas we'd get lucky once in a while. When I was typing and not paying attention to the outside, I could tell when we approached a more populated area--the kismet alerts would start going off every 5 seconds or so. At one point we found 5 Linksys networks within 30 seconds of each other.
In total, there were 104 access points along that stretch of Turnpike. Door to door, we found 112.
Posted by jzawodn at December 25, 2003 11:13 PM | edit
What's the big deal with wardriving? Are people hacking into networks?
To any end though? Or just to get a "feel" for what's out there?
More on the Flying J WiFi install. http://driversmag.com/ar/fleet_flying_continues_wifi/
It's provided by Tonservices, about US$200 a year flat rate or about US$2.00 an hour with out commitment. That's about US$150 a year cheaper than we pay for Wayport or for T Mobile.
Dave
Newbian question - are most of these networks wide open? As in you could log right on to them?
A non-trivial percentage of them are wide open, yes.
Even the ones that use WEP, you can break into with some work. Considering most don't even use WEP, it's obviously easier.
It's a newish kind of thing like Bluejacking, both methods of seeing what's out there, like War dialing! (even that is still done quite a lot)
It's all good fun.
